IBM, one of the world’s leading integrated technology and services company focusing on enterprises agreed to acquire Red Hat Inc for about US$34 Billion. This is a major big-ticket acquisition in the cloud segment. Most companies are looking to adopt cloud for everyday workload, processes consuming cloud based storage infra, services, tools, technologies and big data analytics which means significant opportunities for everyone in the cloud computing value chain. Some of our thoughts below on this acquisition and what it means:
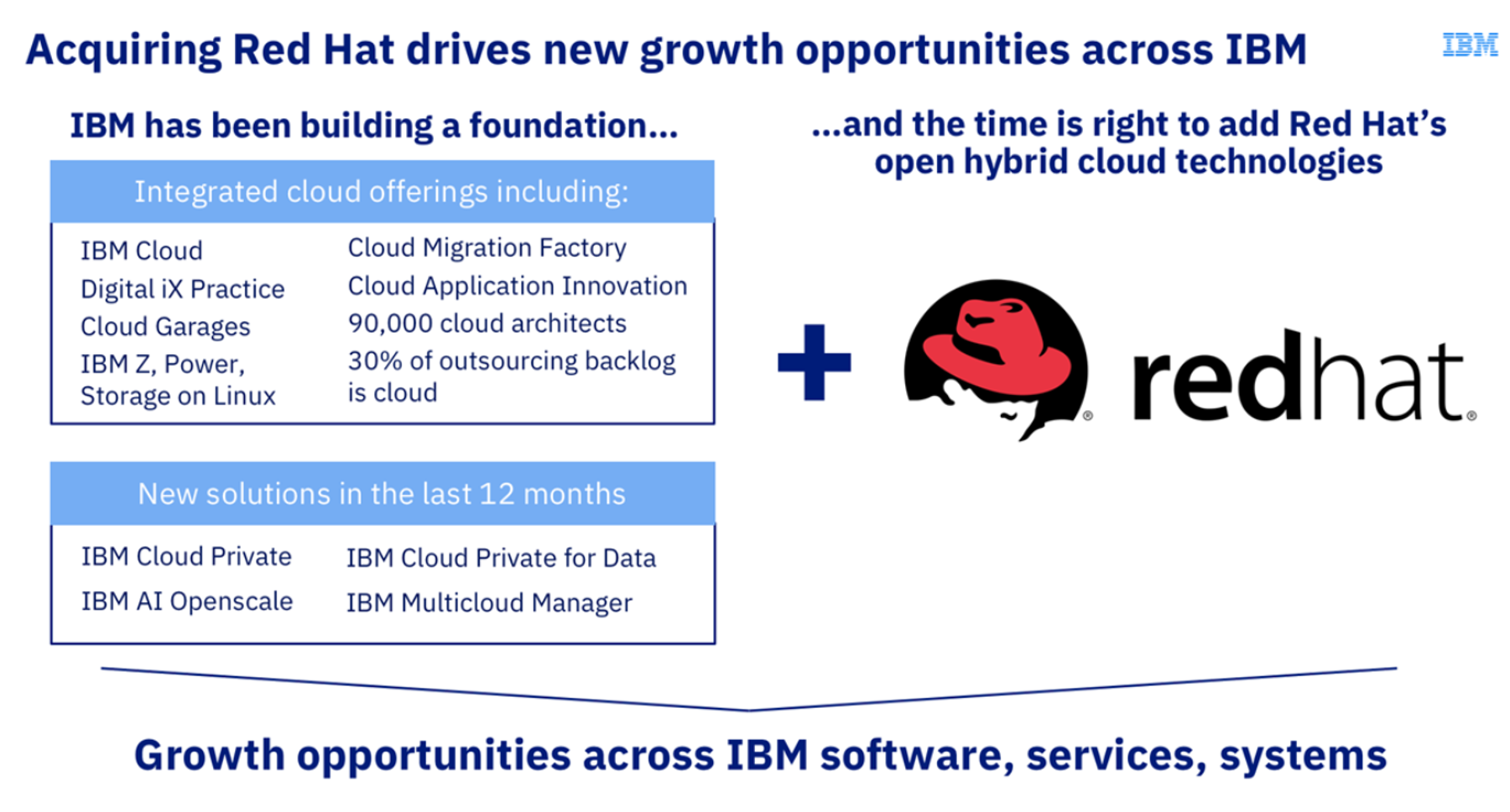
- Since IBM’s business model has pivoted to helping enterprises in their digital transformation journey, building end-to-end cutting edge capabilities from hardware to software to services is key for IBM to scale and grow.
- IBM’s current offerings include a comprehensive suite of innovative solutions and services – Cloud (IBM Cloud Infra and services), AI (IBM Watson), Solutions (Blockchain, Watson IoT, Cognitive and Transaction Processing Software), Enterprise Services (Consulting, Application Management, etc) and more.
- The bigger piece of its portfolio has been the “Technology Services & Cloud Platforms, a US$34 billion per year business along with the US$8 billion per year IBM Systems segment in 2017.
- Together the direct cloud related hardware systems, software integration and services totaling to almost US$42 billion business though more or less flat YoY growth expected in 2018 as well. This has been putting pressure on IBM to strengthen its revenue generation opportunities to enhance the portfolio.
- IBM has been collaborating with Red Hat to drive enterprise-grade Linux software integrations along with the hot trend of “containerization” with Kubernetes to tap the significant growth in edge computing space by offering hybrid-cloud solutions.
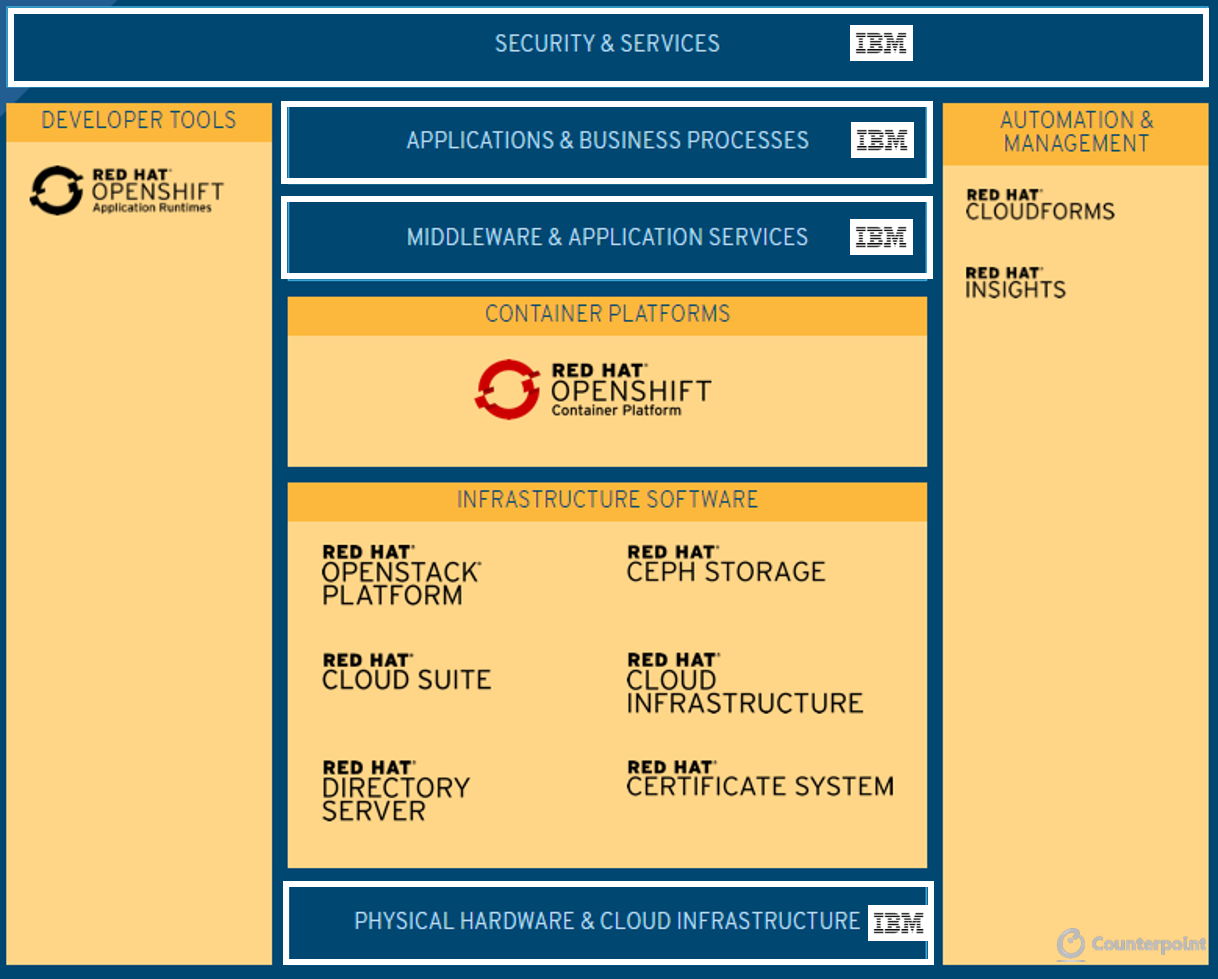
- Thus, RedHat’s offerings nicely complements IBM’s offerings – RedHat offers a stable stream of “software-services subscription revenue” of almost $700 million per quarter (~90% of RedHat’s revenues which is a clear gap in IBM’s portfolio and will be additive to IBM’s top and bottom line).
- RedHat’s OpenShift (containers) and Ansible are fastest growing technologies for the company adding immediate value though there might be some overlap in Middleware & Applications Services segment where IBM is better positioned to drive forward with its existing offerings.
- Overall, this helps IBM become a vertically integrated cloud solution provider by adding an open software driven services model for the modern cloud and data infrastructure.
- For RedHat, this is a great deal to now have ability to be more integrated into IBM’s end-to-end cloud solution and scale faster with IBM’s bigger enterprise footprint.
- RedHat also enjoys a strong mindshare across a vibrant developer community, so this is a great win for IBM as well to court more enterprise developers and cross-sell its multitude of services and solutions.
- However, the cost of acquisition ~$34 billion means IBM will be under pressure to scale this $3 billion per year RedHat business to double every year in order to meet the return over next five years.
- This deal makes for a more formidable and complete cloud player and will help win some big deals. However, IBM still has its work cut out to ensure it succeeds and helps boost the already flattening revenues.
- It also remains to be seen if the RedHat acquisition will turn out as significant as Android acquisition was to Google or the NeXT acquisition was to Apple.
- This adds to IBM’s significant R&D investments in forward looking technologies such as AI, blockchain and IoT, which should hopefully drive some growth over the next few years.
- This will be possible only if IBM scales similar to how Microsoft has successfully scaled the Azure Cloud business targeting different verticals and enterprises from small-medium to large.
- Microsoft and Amazon will be keeping a close eye on how this affects their relationship with RedHat even though most of RedHat’s offerings are open-source.